Cloud Security 101
Welcome to episode #7 of the webcast. A semi-weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »Cloud Security 101
Welcome to episode #7 of the webcast. A semi-weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »Cloud Security 101
Welcome to episode #6 of the webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »White House National Cybersecurity Strategy

Welcome to episode #5 of the webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »Security Risk Management
Welcome to episode #4 of the webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »Zerø Trust
Welcome to episode #3 of the webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth. A show for aspiring and existing cybersecurity leaders.… Read More »So You Wanna Be A CISO
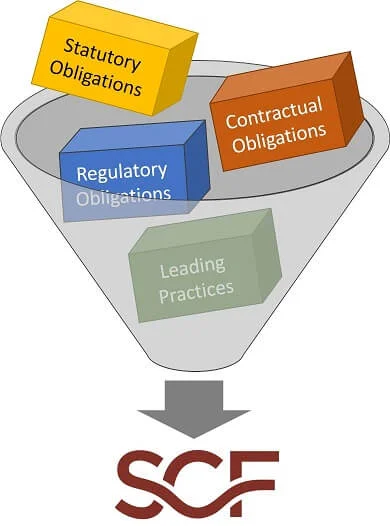
Welcome to the all new webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth, A show for aspiring and existing cybersecurity leaders. Hosted… Read More »Practical uses of the Secure Controls Framework (Part 2)

Welcome to the all new webcast. A weekly livestream, video feed and podcast from Cybersecurity Growth, A show for aspiring and existing cybersecurity leaders. Hosted… Read More »Secure Controls Framework, an introduction (Part 1)
Initially posted at: https://www.nisos.com/podcast/know-your-adversary-episode-3/ I had the privilege to (virtually) sit with my industry colleague, Landon Winkelvoss (co-founder, Nisos) to discuss cyber adversaries I have… Read More »The World of Online Platform Abuse and Fraud
[updated April 12, 2021]You’re a cybersecurity leader at a growing company. [or information security leader — I’ll just say security from here on out]. You… Read More »M&A and Cybersecurity
Securing the Resources, Accounts and Permissions of the Cloud Identity Perimeter The dynamic and ephemeral nature of cloud environments makes traditional security perimeter approaches insufficient… Read More »Cloud IAM Webinar with DivvyCloud